Cracking Passwords with Hashcat
07 May 2017
.
tech
.
Comments
#security
#redteam
#dvwa
Last time, we dumped the dvwa database of DVWA, by exploiting an SQL injection in it. As part of this dump, we extracted the user passwords.
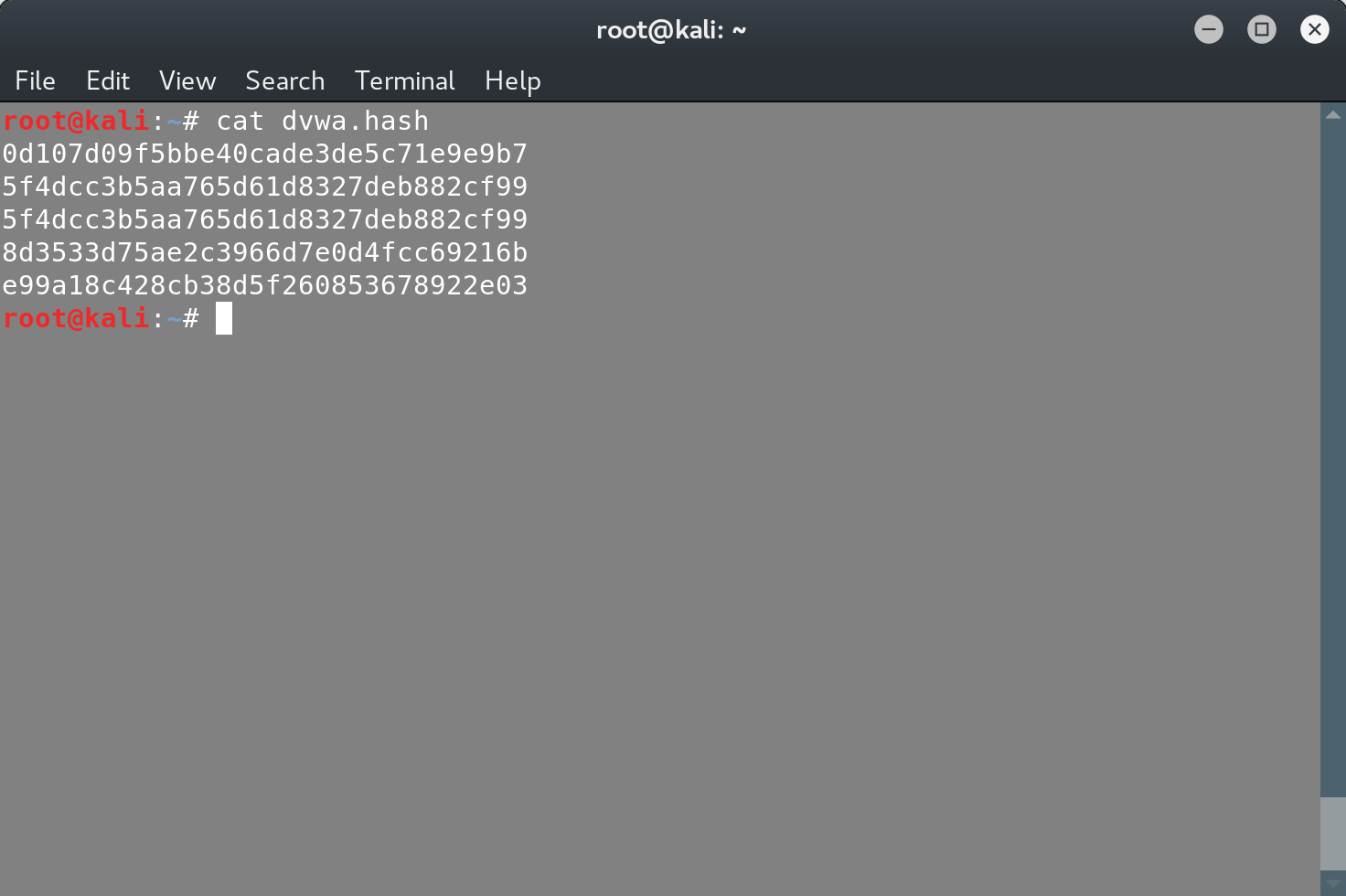
These are not the user passwords themselves, but their hash digest. The hash digests are produced by using a hash function and the most important property of this function, is that it’s a one way function, meaning that it’s impossible to invert. This means that in order to find the original value, given a hash digest, you have to attempt to guess the original value, calculate its digest and then compare it with the value that you are trying to invert. Of course since the hash functions are deterministic, you can also create and store a mapping of values and digests, these are the so-called rainbow tables.
In order to crack these digests, we need to know what cryptographic hash function was used to produce them:
head -n 1 dvwa.hash | hash-identifier
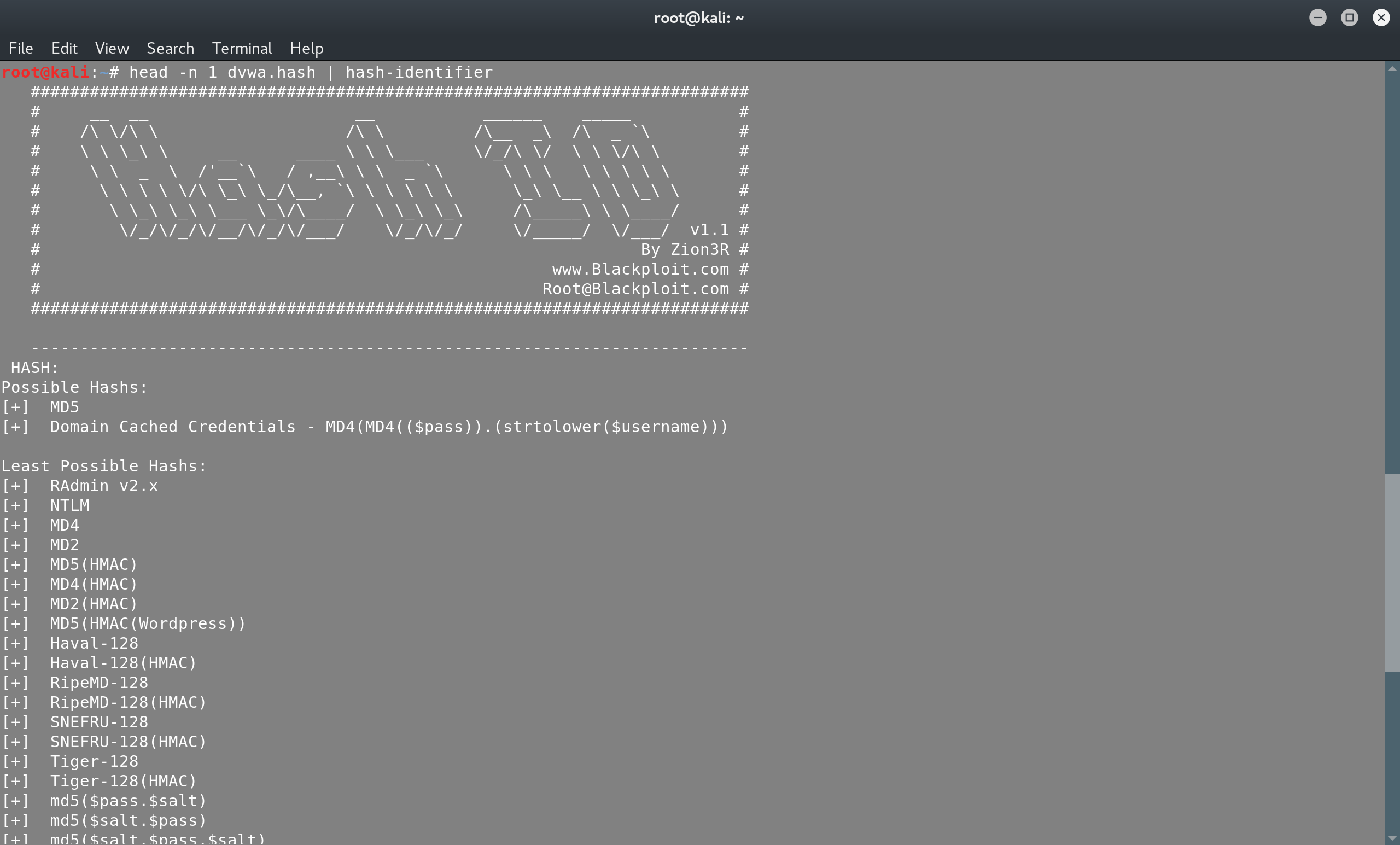
Two possible hashes, but we’ll start with guessing that MD5 was used. If we fail to crack any password, then we should consider trying the Domain Cached Credentials option.
Now we’re good to get our hands on hashcat. The main reason hashcat is powerful, is because it will take advantage of the GPUs of the system that is running on. Of course you can always rent some cloud solution that offers GPU processing power, in order to add some more muscle to your rig.
Hashcat has different attack modes, some of them being straight, combination and brute-force. The straight attack mode will compute the hashes for all the words that hashcat will find in the wordlist. The combination mode will try combinations of the words that are in the wordlist, and the brute-force attack will blindly try all the possible combinations. The brute-force mode is not useful for passwords longer than 10 characters due to the combinatorial explosion of the search space.
From the help menu of hashcat, you can find the code that corresponds to the hash function that you will attack, in our case it’s 0 for MD5:
hashcat --help
We’ll try to crack the DVWA passwords with a simple straight attack mode (it’s DVWA after all..) and we’ll use a simple wordlist of sqlmap:
hashcat -m 0 -a 0 dvwa.hash /usr/share/wordlists/sqlmap.txt
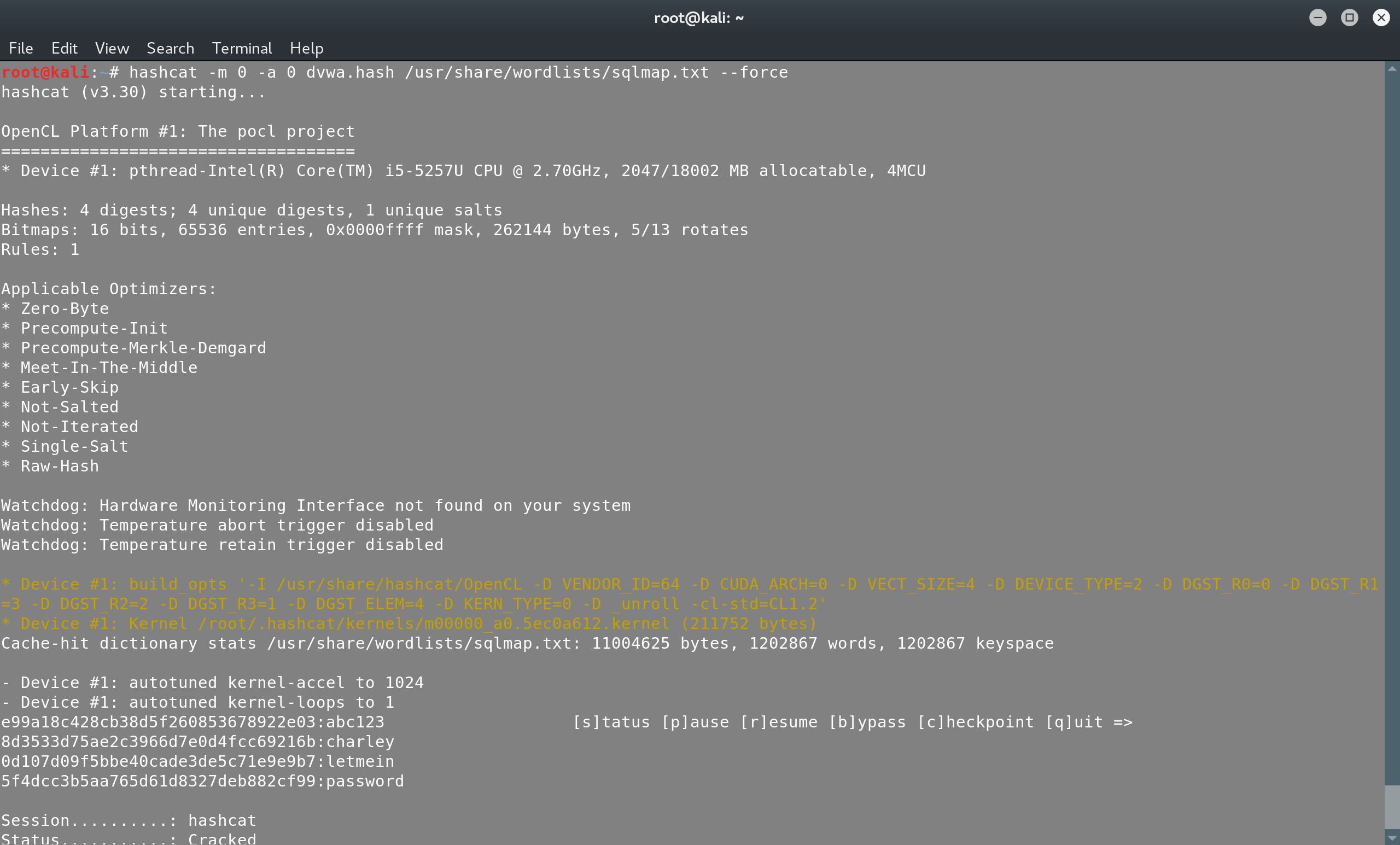
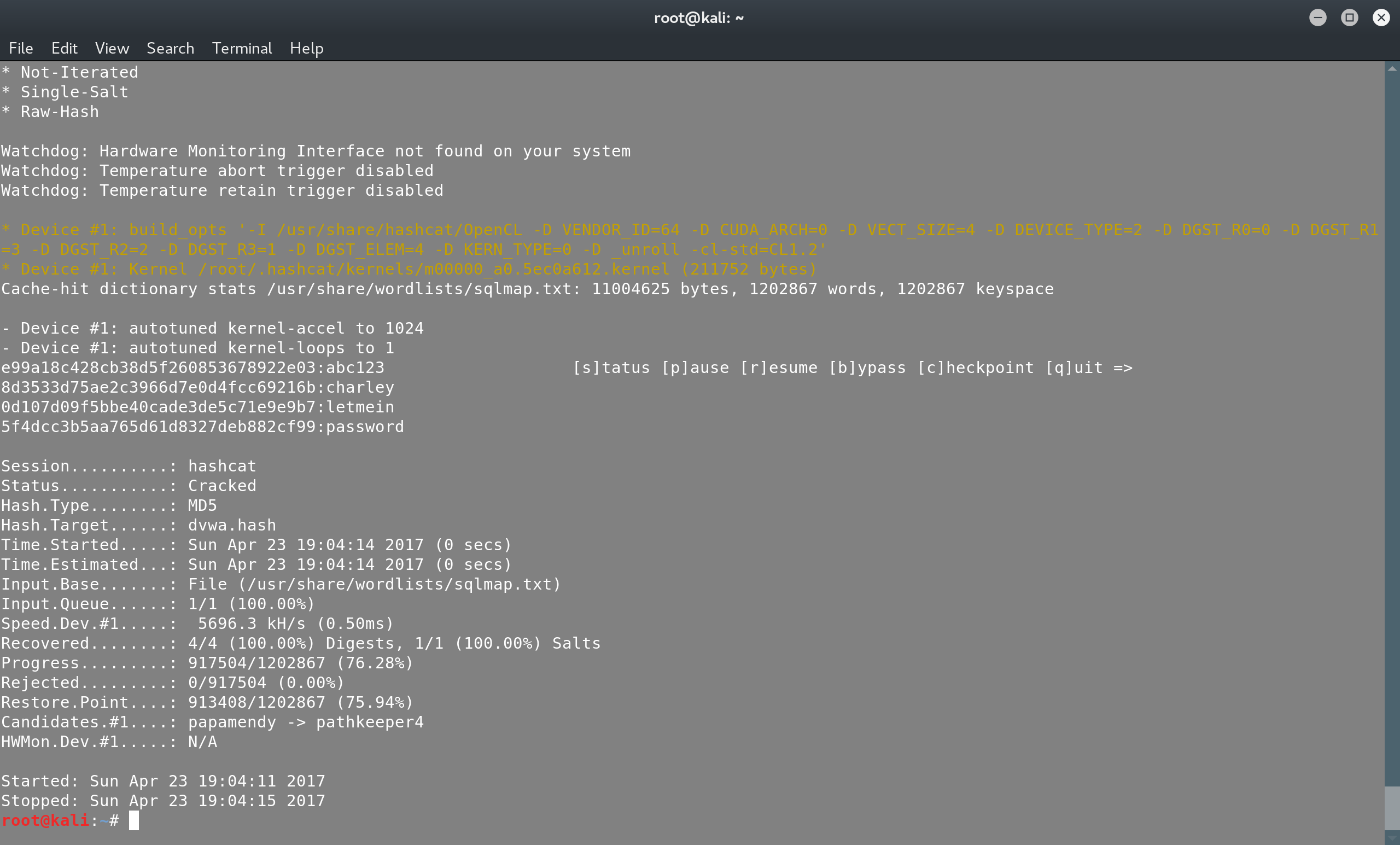
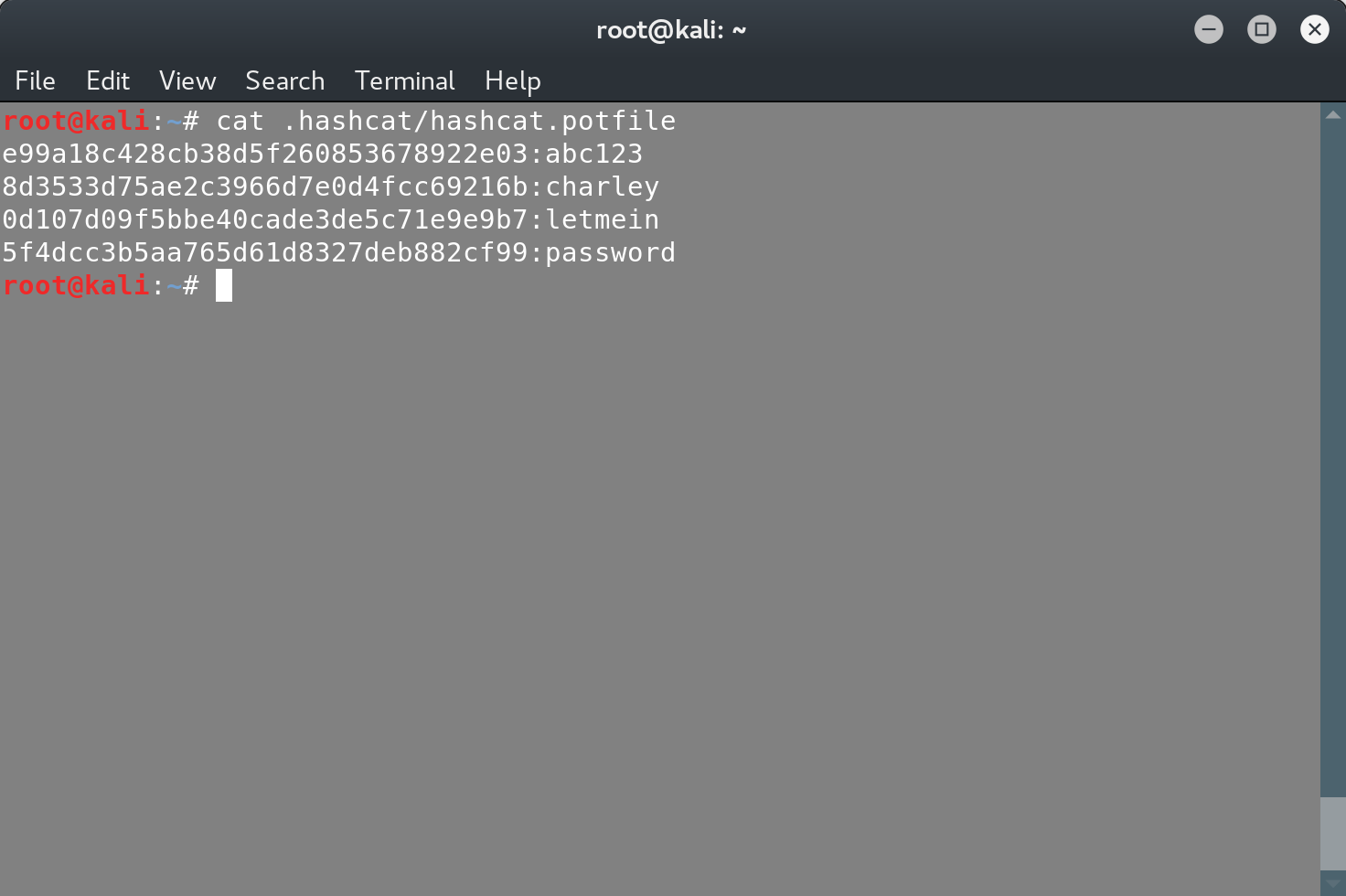
And just like that we’ve recovered the passwords. Note that hashcat creates a potfile, where it stores all the passwords that have been recovered:
In the future we’ll see more sophisticated usages of hashcat, in order to break stronger passwords, which include numbers, capital letters and special characters and phrases.
